Cybersecurity researchers have discovered that the upgraded AgentTesla, an information-gathering malware, is now capable of stealing Wi-Fi passwords from compromised computers.
“AgentTesla is a .Net-based infostealer that has the capability to steal data from different applications on victim machines, such as browsers, FTP clients, and file downloaders. The actor behind this malware is constantly maintaining it by adding new modules,” wrote Malwarebytes researcher Hossein Jazi in a blog post.
For those unaware, AgentTesla was first seen in 2014, and has been ever since frequently used by cybercriminals in various malicious campaigns. During the months of March and April 2020, it was actively distributed through spam campaigns in different formats, such as ZIP, CAB, MSI, IMG files, and Office documents.
Also Read- Best Wifi Hacking Tools
Newer variants of AgentTesla seen in the wild have the capability to collect information about a victim’s Wi-Fi profile.
The variant analysed by Malwarebytes was written in .Net and has an executable embedded as an image resource, which is extracted and executed at run-time. This executable also has an encrypted resource. After doing several anti-debugging, anti-sandboxing, and anti-virtualization checks, the executable decrypts and injects the content of the resource into itself.
The second payload is the main component of AgentTesla that steals credentials from browsers, FTP clients, wireless profiles, and more. The sample is heavily obfuscated to make the analysis more difficult for researchers.
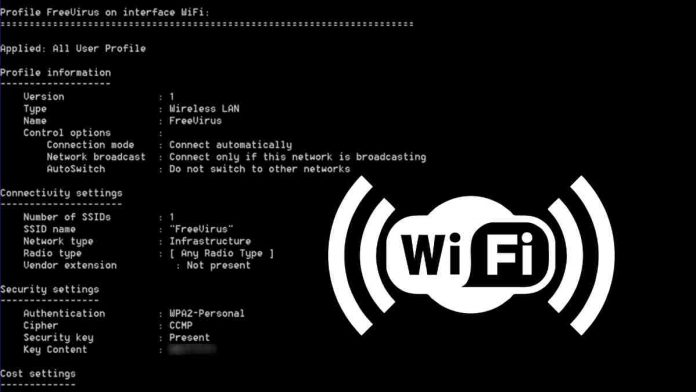
To steal Wi-Fi profile credentials, a new “netsh” process is created by passing “wlan show profile” as argument.
“Available Wi-Fi names are then extracted by applying a regex: “All User Profile * : (?<profile>.*)”, on the stdout output of the process,” Hossein explains.
A command is then executed to extract each wireless profile’s credential: “netsh wlan show profile PRPFILENAME key=clear”
In addition to Wi-Fi profiles, the malware can also collect data about the target system, including FTP clients, browsers, file downloaders, and machine info (username, computer name, OS name, CPU architecture, RAM).
“We believe the threat actors may be considering using Wi-Fi as a mechanism for spread, similar to what was observed with Emotet,” said Malwarebytes. “Another possibility is using the Wi-Fi profile to set the stage for future attacks.”
AgentTesla is not the first malware to update to steal Wi-Fi passwords. Previously, the infamous Emotet malware was used to hack into Wi-Fi networks to infect connected computers.
It is not clear as to why AgentTesla added the Wi-Fi stealing feature. According to Hossein, the threat actors may be considering using Wi-Fi as a mechanism for spread, similar to what was observed with Emotet. Another possibility could be to use the Wi-Fi profile to set the stage for future attacks.