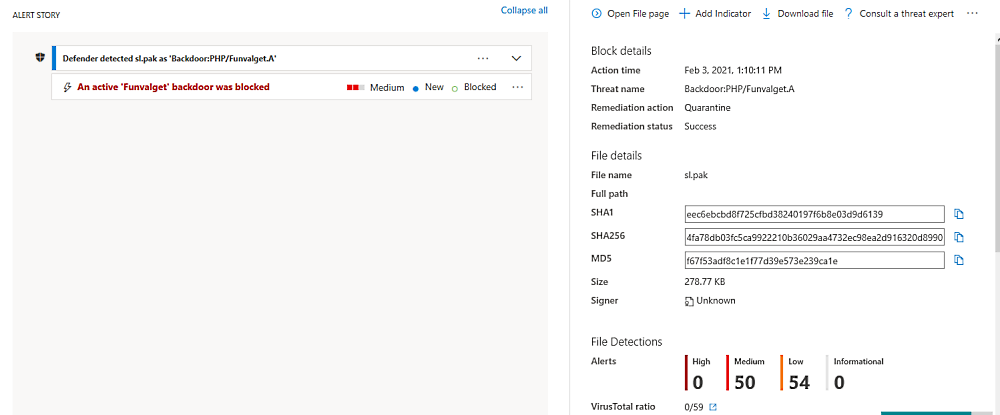
Microsoft Defender for Endpoint [previously known as Microsoft Advanced Threat Protection (ATP)] is detecting the latest update for the Google Chrome browser as a backdoor trojan.
On Tuesday, Google had released the latest version of the Chrome browser 88.0.4323.146 for Windows, MacOS and Linux to patch several security loopholes.
As first reported by ZDNet, according to the screenshot shown above, Defender ATP is detecting the Chrome sl.pak language file in both Chrome 88.0.4324.104 and 88.0.4323.146as containing a generic backdoor trojan named “PHP/Funvalget.A.”
Several users using the Microsoft Defender ATP security platform took to Twitter to report the issue and question Microsoft if the detections were “false positives”.
ATP is triggering on C:Program Files (x86)GoogleChromeApplication88.0.4324.146Localessk.pak
— Dark Defender (@ShadyDefender) February 3, 2021
Hey @msftsecresponse – Seeing lots of Defender ATP alerts this morning on C:Program Files (x86)GoogleChromeApplication88.0.4324.104Localessl.pak detected as PHP/Funvalget.A. Can you confirm this is a false positive? SHA256 in reply.
— W. David Winslow (@wdwinslow) February 3, 2021
Defender detected sl.pak as 'Backdoor:PHP/Funvalget.A'
C:Program FilesGoogleChromeApplication88.0.4324.146Localessl.pak
Defender detected chrome.7z as 'Backdoor:PHP/Funvalget.A'
C:Program FilesGoogleChromeApplication88.0.4324.146Installerchrome.7z— itquartz (@itquartz) February 3, 2021
Microsoft acknowledged the issue stating it was an automation error and it is now resolved.
“We’ve corrected an automation error that incorrectly classified the installation package as malware,” said a Microsoft spokesperson.
To clear the current cache and trigger an update, system admins are advised to use a batch script that runs the following commands as an administrator to unblock the installer for the latest Chrome version:
cd %ProgramFiles%\Windows Defender
MpCmdRun.exe -removedefinitions -dynamicsignatures
MpCmdRun.exe -SignatureUpdate