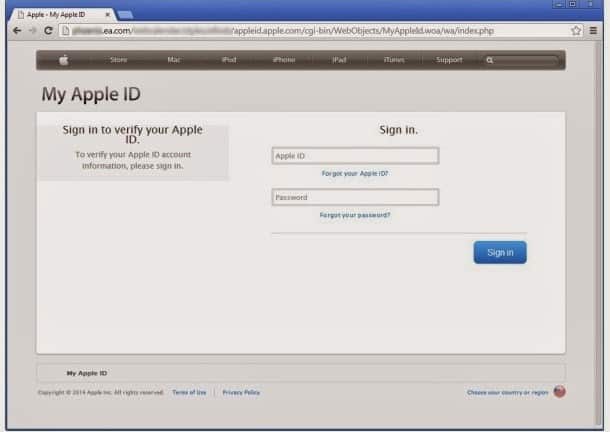
A report published by Netcraft says that cyber criminals have managed to hack two websites hosted on a Electronic Arts (EA) server. And then they proceeded to use those two websites for phishing Apple users. The image below is of the website which is hosting the phishing page.
.
.
EA or Electronic Arts is a world renowned game developer and publisher of Video, PC and mobile games. EA develops and publishes games under several labels including EA Sports titles, Madden NFL, FIFA, NHL, NCAA Football, NBA Live, and SSX. This makes EA one of the trusted brands world wide and any page from EA asking for your credentials is bound to be prod user to give them without any second though.
This is exactly what the hackers have managed to achieve. Netcraft reports that the attackers have hacked into a server that hosts two websites on the ea.com domain. The server in question hosts a calendar based on WebCalendar 1.2.0. This is an old version of the software (2008), so it’s full of vulnerabilities that could have been exploited by the hackers. For instance, the attackers could have leveraged CVE-2012-5385, which can be exploited to modify settings and possibly even execute code.
This is exactly what the hackers have managed to achieve. Netcraft reports that the attackers have hacked into a server that hosts two websites on the ea.com domain. The server in question hosts a calendar based on WebCalendar 1.2.0. This is an old version of the software (2008), so it’s full of vulnerabilities that could have been exploited by the hackers. For instance, the attackers could have leveraged CVE-2012-5385, which can be exploited to modify settings and possibly even execute code.
“It is likely that one of these vulnerabilities was used to compromise the server, as the phishing content is located in the same directory as the WebCalendar application,” Netcraft’s Paul Mutton noted in a blog post.
The phishing page is designed to mimic the My Apple ID login page. First, victims are instructed to enter their Apple ID and their password. Then, they’re asked to hand over their name, payment card number, expiration date, CVV, date of birth and other personal information.
Once the information is provided to the cybercriminals, victims are redirected to Apple’s genuine website, most likely in an effort to avoid raising any suspicion.
“The compromised server is hosted within EA’s own network. Compromised internet-visible servers are often used as ‘stepping stones’ to attack internal servers and access data which would otherwise be invisible to the internet, although there is no obvious outward facing evidence to suggest that this has happened,” Mutton explained.
“In this case, the hacker has managed to install and execute arbitrary PHP scripts on the EA server, so it is likely that he can at least also view the contents of the calendar and some of the source code and other data present on the server,” he added.
“The mere presence of old software can often provide sufficient incentive for a hacker to target one system over another, and to spend more time looking for additional vulnerabilities or trying to probe deeper into the internal network.”