Next time you receive a SMS from the freight carriers DHL about a delivery /impending delivery of a package or parcel, do be careful. In a report published on McAfee Blog, security researchers have observed that short text messages (SMS) sent by DHL, claiming to be a tracking notification of your package, actually delivers a vicious Android malware to your smart phone. This particular SMS spam has been noticed only in Germany so far.
Readers will note that using tracking notification as a spamming method is as old as the email itself with mostly all reputable couriers such as RMS, DHL, FedEx, or UPS being used to usurp unsuspecting victims money. However this is the first time, the researchers note that a SMS is being used to distribute malware in Android using this method.
Researchers at McAfee Labs have noticed this trend is currently targeting users in Germany, where they receive malware stored in the cloud storage provided by Dropbox. The malicious file is an installer package with the name “DHL.apk” and it is delivered through a shared link that is masked via Google’s URL shortening service.
According to McAfee, the German SMS reads “Ihr DHL Packung ist ihnen geliefert, verfolgen Sie online über,” followed by the URL to the malicious download. Translated, this informs that the DHL parcel has been delivered and it can be tracked via the provided link. This provides a very good motive for victims to click on the link and download the malware.
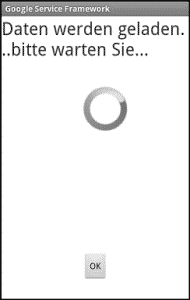
After installation, the malware does what a normal malware is supposed to do. It takes over the Google Service Framework, shuts it down and then assumes its place on the home screen. At the first launch, the user is asked to allow it administrator privileges.
The security researchers at McAfee have named the malwar as Android/SmsHnd.A. The malware after installation and getting user privileges initiates a background service for establishing communication with the command and control server, from where it receives instructions on what to steal from the device. According to the researchers, it can,
- Leak sensitive device information (phone number, device model, IMEI, and IMSI)
- Send SMS messages using data (phone number and text) provided by the remote server
- Send a specific text message to all the phone and SIM contacts
- Steal the contact list
Moreover, the cybercriminals have devised it to be able to send short text messages with information (phone number and text) received from the command and control server. It can also be used to further spread the malware by sending it to the victims contacts in the address book.
“In addition to these actions, every time an SMS message is sent to the infected device (but not from any of the numbers from the victim’s contact list), it will be intercepted and forwarded to a remote server,”
 |
| Image source McAfee Blog |
One reason for this would be to intercept the two-factor authentication codes sent to the victim to log into online banking accounts. The McAfee researchers have also found out that the remote Command and Control server is based somewhere in Japan and further investigations are going on.

