This smart building was hacked by IBM researchers to show hacking risks associated with Internet of Things
IBM security researchers are warning that building automation systems used to power so-called “smart buildings” pose a security risk to companies. According to Gartner, devices in smart homes and smart commercial buildings represented 45 percent of total connected things in use in 2015.
According to a new IBM X-Force report, all the appliances in an office that is controlled by smart devices is being countered by the inherent threat these devices can pose to the network to which they are attached. The ones that control your building’s heating, lighting and air conditioning are also no exception.
The IBM security researchers as part of a penetration test they carried out on their own initiative, chose a random building that had implemented smart IoT solutions for its employees, and hacked into its infrastructure just to prove a point about the lack of proper security measures in smart building and smart office environments.
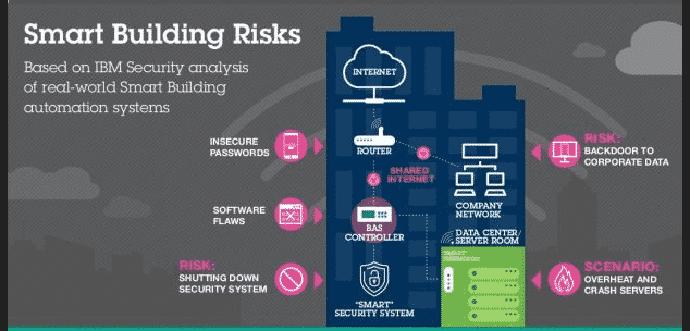
Most of today’s BAS (Building Automation Systems) work in the same manner. Each building has a BAS controller, responsible for managing each of the building’s “smart” features and for collecting and aggregating data from various sensors (humidity, temperature, light, etc.). This BAS controller connects to the Internet through local Wi-Fi spots and the building router, where, in some cases, it sends data to manufacturers or central company servers that gather information from different buildings across the country.
“Little attention is being paid to the potential cybersecurity risks created by smart office technology since these devices fall outside the scope of traditional IT. In fact, a recent survey of building automation system (BAS) operators found that only 29 percent had taken action or were in the process of taking action to improve cybersecurity for their Internet-connected systems,” X-Force researcher Paul Ionescu wrote in a blog.
To prove this point, Ionescu and other X-Force researchers put their skills to the test by conducting an ethical hacking exercise against a “smart office” in North America. The test was conducted with the aim of cracking into its main monitoring and control server that controls not only the building in question but also other locations in North America.
“We were surprised by the amount of very basic security errors that we found which allowed us to break into the system. Things like shared passwords and information stored in clear text within the devices made it significantly easier for us to eventually hack into the central command server, along with the vulnerabilities we identified in the router and BAS software,” Ionescu said to SCMagazine.com in an email.
A flaw in the system diagnostics page in the building automation software allowed the X-Force researchers to access configuration settings for the device, including encrypted passwords. From there, they were able to decrypt the passwords and discover the password for the central command server, which controls stations for several buildings across North America, he said.
The attackers then drove by the facility where the software was deployed and were able to gain access to the central command server by using that password and connecting to the system from outside the building through the Wi-Fi network, he added.
Not only this, the IBM researchers were able to change the basic environmental controls in all the buildings, but also door locks, fire alarms, security systems and even refrigeration units leaving the building susceptible to a physical burglary, Ionescu noted.
IBM said that the combination of weak security, Internet connectivity and vulnerable systems is common in the building management sector, exposing companies that own or even rent in modern office buildings to attack, said Diana Kelly, Executive Security Advisor at IBM.
IBM worked with the company to strengthen its security protocols but also reported the susceptibilties it discovered to the BAS manufacturer.
The experiment has brought to light a lot of points, which the team shares in its Penetration Testing a Building Automation System report, and plans to present at the InterConnect 2016 security conference.