Researcher discloses an unpatched KDE vulnerability that can run malicious code on a user’s system
A security researcher has published a proof-of-concept (POC) code on Twitter for a zero-day vulnerability in the KDE software framework that is yet to be fixed.
The security expert, Dominik Penner aka “@zer0pwn” who discovered the problem said that the vulnerability affects KDE Frameworks version 5.60.0 and below.
For those unaware, KDE Frameworks is a collection of libraries and software frameworks that are at the base of the KDE desktop environment v4 and v5 (Plasma).
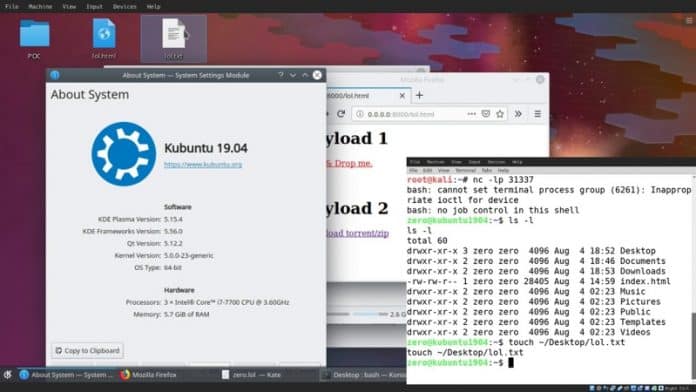
According to Penner, there is a command injection vulnerability in KDE 4/5 Plasma desktop due to the way the KDesktopFile class (part of KDE Frameworks) handles .desktop and .directory files. This allows the malicious code stored within the .desktop and .directory files to silently run arbitrary code on a user’s computer without the user having to interact or open files.
“KDE 4/5 is vulnerable to a command injection vulnerability in the KDesktopFile class. When a .desktopor .directory file is instantiated, it unsafely evaluates environment variables and shell expansions using KConfigPrivate::expandString() via the KConfigGroup::readEntry() function,” reads a post published by Penner.
“Using a specially crafted .desktop file a remote user could be compromised by simply downloading and viewing the file in their file manager, or by drag and dropping a link of it into their documents or desktop.”
Penner explained that when a user opens the KDE file viewer to access the directory where these files are stored, it results in the execution of the malicious code in the .desktop and .directory files.
“When we combine this /feature/ with the way KDE handles .desktop and .directory files, we can force the file to evaluate some of the entries within the [Desktop Entry] tag,” Penner added. “Some of the entries in this tag include “Icon”, “Name”, etc. The exploit is dependent on the entry that gets read by the KConfigGroup::readEntry() function.”
The researcher says the vulnerability can be used by attackers to drop shell commands inside the standard “Icon” entries found in .desktop and .directory files.
“So for example, if we were to browse to the malicious file in our file manager (dolphin), the Icon entry would get called in order to display the icon,” he said.
“Since we know this, we can use shell command in place of the Icon entry, which in turn will execute our command whenever the file is viewed. Theoretically, if we can control config entries and trigger their reading, we can achieve command injection / RCE.”
Penner also published the exploit code for the vulnerability along with two videos (see below) demonstrating the attack scenarios that exploit the KDE KDesktopFile Command Injection vulnerability:
It appears that the researcher did not notify KDE developers about the vulnerability before publishing details about the bug to the public. Meanwhile, the KDE team have acknowledged the vulnerability and are currently working on a fix.
“For the moment avoid downloading .desktop or .directory files and extracting archives from untrusted sources,” KDE Community said to users. “Also, if you discover a similar vulnerability, it is best to send an email [email protected] before making it public. This will give us time to patch it and keep users safe before the bad guys try to exploit it,” the KDE developers recommended.