Security researchers at Zscaler’s ThreatLabz group have discovered a new strain of a large-scale phishing campaign, which uses an adversary-in-the-middle (AiTM) attack technique capable of bypassing multi-factor authentication (MFA).
For the unversed, AiTM attack is a cyberattack where the attacker secretly conveys and possibly alters the communications between two parties who believe that they are directly communicating with each other, as the attacker has inserted themselves between the two parties. Hackers through this method can use the stolen cookies to log in and completely evade MFA.
The main purpose of the large-scale phishing campaign is believed to be breaching of corporate accounts to conduct BEC (business email compromise) attacks, which redirects payments toward the hacker’s bank account using forged documents, as reported by BleepingComputer.
ThreatLabz describes the new phishing attack as highly sophisticated. It “uses an adversary-in-the-middle (AiTM) attack technique capable of bypassing multi-factor authentication” and “multiple evasion techniques used in various stages of the attack designed to bypass conventional email security and network security solutions”.
The main targets of the phishing campaign include various industries, such as FinTech, Lending, Finance, Insurance, Accounting, Energy, and Federal Credit Union organizations. Most of the targeted organizations are based in the U.S., UK, New Zealand, and Australia.
According to Zscaler’s ThreatLabz researchers, the campaign is still active, and the threat actors are creating new phishing domains almost every day.
Details Of Phishing Campaign
The ongoing campaign was originally detected by researchers at ThreatLabz in June 2022, with analysts observing an increase in the use of advanced phishing kits in a large-scale campaign against specific sectors and account holders of Microsoft email services.
All these phishing attacks begin with an invoice-themed email sent to the victim containing a malicious link embedded either as buttons in the message body or within the attached HTML files that trigger redirections to the phishing pages.
Once the email recipient opens the attachment via a web browser, it redirects the target to a phishing page that impersonates a login page for Microsoft Office but not before fingerprinting the compromised machine to determine whether the page visitor is a targeted victim of the campaign or someone else.
There are different methods used in this campaign to make it stand out, which include open redirect pages hosted by Google Ads, Snapchat, and DoubleClick. The aim of the hackers is to load the phishing URL so that it can fool the user to click on it. Unfortunately, some platforms don’t see open redirects as a vulnerability, leaving them available for abuse by threat actors.
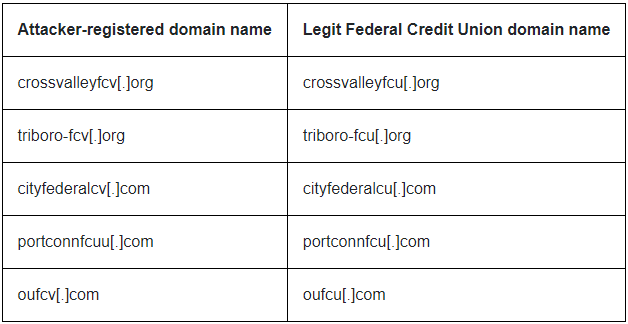
Some of the attacker-registered domains were typo-squatted versions of legit Federal Credit Unions in the U.S., as shown in the table below:
“Per our analysis of the original emails using the Federal Credit Union theme, we observed an interesting pattern. These emails originated from the email addresses of the chief executives of the respective Federal Credit Union organizations,” the ThreatLabz report on the new phishing campaign said.
“This indicates that the threat actor might have compromised the corporate emails of chief executives of these organizations using this phishing attack and later used these compromised business emails to send further phishing emails as part of the same campaign.”
Further, some of the domain names used keywords related to “password reset” and “password expiry” reminders, as part of their email phishing campaigns:
expiryrequest-mailaccess[.]com
expirationrequest-passwordreminder[.]com
emailaccess-passwordnotice[.]com
emailaccess-expirynotification[.]com
It is important to note that there are several other domains involved in this active campaign, some of them are completely randomized while others do not conform to any specific pattern.
The campaign uses several redirection techniques, wherein legitimate online code editing services such as CodeSandbox and Glitch are abused to increase the shelf life of the campaign.
“A common method of hosting redirection code is making use of web code editing/hosting services: the attacker is able to use those sites, meant for legitimate use by web developers, to rapidly create new code pages, paste into them a redirect code with the latest phishing site’s URL, and proceed to mail the link to the hosted redirect code to victims en masse,” the report added.
Business email compromise (BEC) continues to be one of the top threats, that organizations need to protect against. The threat actors are continuously updating their tactics, techniques, and procedures (TTPs) to bypass various security measures.
To protect against these phishing attacks, security features such as multi-factor authentication (MFA) should not be considered a silver bullet, ThreatLabz said. With the use of advanced phishing kits (AiTM) and clever evasion techniques, threat actors can bypass both traditional as well as advanced security solutions.
As an extra precaution, the Zscaler ThreatLabz researchers have recommended users not open attachments or click on links in emails sent from untrusted or unknown sources. They have also suggested that users should verify the URL in the address bar of the browser before entering any credentials.