Security researchers have discovered a new Android banking trojan that can steal users’ sensitive information and allow attackers to remotely control infected devices.
“Brokewell is a typical modern banking malware equipped with both data-stealing and remote-control capabilities built into the malware,” Dutch security firm ThreatFabric said in an analysis published on Thursday.
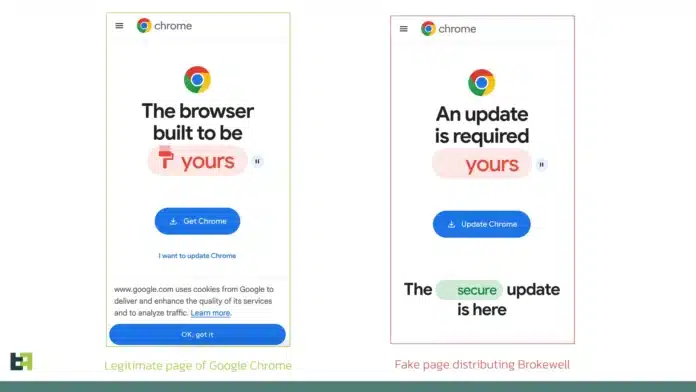
According to ThreatFabric, Brokewell poses a significant threat to the banking industry, providing attackers with remote access to all assets available through mobile banking. The malware was discovered by the researchers while investigating a fake Google Chrome web browser “update” page, commonly used by cybercriminals to lure victims into downloading and installing malware.
Looking at prior campaigns, the researchers found that Brokewell was used to target a popular “buy now, pay later” financial service and an Austrian digital authentication application.
The malware is said to be in active development, with new commands added almost daily to capture every event on the device, from keystrokes and information displayed on screen to text entries and apps launched by the victim.
Once downloaded, Brokewell creates an overlay screen on a targeted application to capture user credentials. It can also steal browser cookies by launching its own WebView, overriding the onPageFinished method, and dumping the session cookies after the user completes the login process.
“Brokewell is equipped with “accessibility logging,” capturing every event happening on the device: touches, swipes, information displayed, text input, and applications opened. All actions are logged and sent to the command-and-control server, effectively stealing any confidential data displayed or entered on the compromised device,” the ThreatFabric researchers point out.
“It’s important to highlight that, in this case, any application is at risk of data compromise: Brokewell logs every event, posing a threat to all applications installed on the device. This piece of malware also supports a variety of “spyware” functionalities: it can collect information about the device, call history, geolocation, and record audio.”
After stealing the credentials, the attackers can initiate a Device Takeover attack using remote control capabilities to perform screen streaming. It also provides the threat actor with a range of various commands that can be executed on the controlled device, such as touches, swipes, and clicks on specified elements.
ThreatFabric discovered that one of the servers used as a command and control (C2) point for Brokewell was also used to host a repository called “Brokewell Cyber Labs,” created by a threat actor called “Baron Samedit.”
This repository comprised the source code for the “Brokewell Android Loader,” another tool from the same developer designed to bypass restrictions Google introduced in Android 13 and later to prevent exploitation of Accessibility Service for side-loaded apps (APKs).
According to ThreatFabric, Baron Samedit has been active for at least two years, providing tools to other cybercriminals to check stolen accounts from multiple services, which could still be improved to support a malware-as-a-service operation.
“We anticipate further evolution of this malware family, as we’ve already observed almost daily updates to the malware. Brokewell will likely be promoted on underground channels as a rental service, attracting the interest of other cybercriminals and sparking new campaigns targeting different regions,” the researchers conclude.
Hence, the only way to effectively identify and prevent potential fraud from malware families like the newly discovered Brokewell is to use a comprehensive, multi-layered fraud detection solution that is based on a combination of indicators, including device, behavior, and identity risks for each customer.
In order to protect yourself from Android malware infections, it is advisable to avoid sideloading apps or opening short URLs in text messages and be very cautious while giving permissions to the apps you install. Further, do not download apps or app updates on your Android phone from outside the Google Play Store.
Additionally, keep Google Play Protect enabled on your Android device at all times to scan all your current apps and any new apps you download for malware. You may also consider installing additional Android antivirus software for added security.
Google has confirmed to Securityweek that Google Play Protect, which is on by default on Android devices with Google Play Services, automatically protects users against known versions of this malware.
It also warns users or blocks apps known to exhibit malicious behavior, even when those apps come from sources outside of Play.